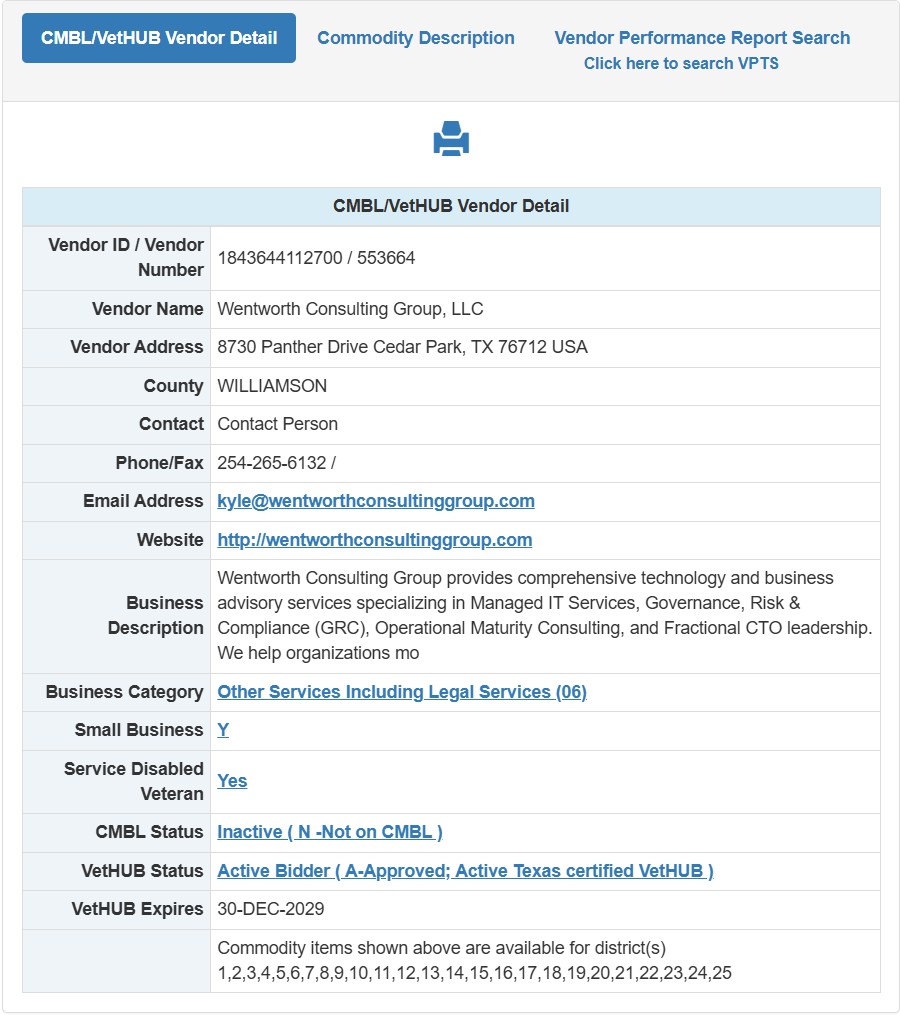
Managing your technology infrastructure is an expensive business. Salaries for a qualified CTO & CIO range between $90K-$250K. The salary for a Certified CISO will range from $105K-$255K. A Business Process Modeler’s salary ranges from $77K-$161K and can reach as high as $200K.
A typical Business Process Modeling project can take 1-3 years. Contract labor costs for the project can range from $50K to $1M+ without the implementation of an ERP (Enterprise Resource Planning) solution. Internal resource costs and expectations are high and demanding during BPM and ERP projects. You need a team that understands how to incorporate your Business Process and Technology Process Models into a working powerhouse toolset that your employees don’t despise when the project is done.
Wentworth Consulting Group simplifies this structure with an easy to understand, monthly recurring cost model based on the size of your organization. This allows for easy understanding and budgeting of all of the services that we provide. We also understand that a well-developed technology infrastructure will continue running once it’s set in motion. With proper monitoring, maintenance and upgrade schedules, your IT infrastructure will require less senior management time in the future than in the beginning of our engagement. This allows us to keep the costs down while we continue to be a part of the technology and business management process.
Get in Touch
- Chief Technology Officer (CTO) – Think Hardware, Software, Network, Wireless, Firewalls, Internet, Cloud, VPN, Servers, Storage, Workstations, Laptops … The stuff that everyone works on and the parts that help them communicate. Planning, designing, overseeing implementation, Business Continuity (formerly disaster recovery and backup) are all the CTO’s responsibility.
- Chief Information Officer (CIO) – Think “How Software is Used”, Software Design, Data and Information (not the storage of that data), Data Access Methods and Security Levels, Data Analysis, Data Collaboration, Data Sharing Internally & Externally.
- Chief Information Security Officer (CISO) – Think Security, Physical Security, Data Security, Internal / External Access Methods, Passwords, Data Breach Detection, Dark Web Monitoring, SPAM/Malware/Ransomware Filtering, End-User Training and Testing.
Key Responsibilities
Specifics of the CTO’s job responsibilities vary from one organization to another. The following are the typical requirements in a CTO job description:
Tech Strategy: (Resources)
- Monitor technological, social and scientific trends that could influence the company’s business goals.
- Identify opportunities and risks for the business.
- Participate in management decisions about corporate governance.
Research and Development:
- Maintain current information about technology standards and compliance regulations.
- Manage research and development of technology, IT assets and associated revenue.
Evangelism:
- Communicate the company’s technology strategy to partners, management, investors and employees.
- Assist with the recruitment, retention, acquisition and sales efforts of the company. Build relationships with vendors, communities and customers.
Key Responsibilities
Specifics of the CIO’s job responsibilities vary from one organization to another. The following are the typical requirements in a CIO job description:
Tech Strategy: (Data & Collaboration)
- Strategic planning of business growth objectives
- Create business value through technology use
- Ensure technology systems and procedures lead to outcomes in line with business goals
- Work with Business Process Modeler to ensure software aligns with usage requirements
- Oversee the development, usage and training of end user software platforms
Research and Development:
- Information risk management (IRM)
- Work together with the CTO to develop IT policies, strategies, and standards
- Review Business Process Model (BPM) and Application Process Model (APM) inconsistencies and plan performance enhancements
- Work with CTO to develop and approve technology futures and budgets
Evangelism:
- Participate in management decisions about corporate governance
- Encourage continuing training and testing of implemented technology solutions
Key Responsibilities
CISO responsibilities focus on security strategy, intellectual property and data protection, awareness training, and threat monitoring and prevention. The following are the typical requirements in a CISO job description:
Tech Strategy: (Internal & External, Physical & Data Security)
- Identifying, planning, strategizing, and implementing security platforms to protect corporate interests
- Frequently uses automated and manual security testing procedures
- Implements and monitors data loss / fraud prevention and data forensic investigation solutions
- Governance and compliance management to promote smooth business operations
Research and Development:
- Cyber risk management and cyber threat intelligence monitoring throughout the tech world
- Work together with the CTO & CIO to prioritize and develop IT policies, strategies, and standards
- Plans and implements security awareness training and retraining of all staff members
- Monitors Dark-Web activity for corporate and company employee compromised data
Evangelism:
- Interacts directly with the Board of Directors and corporate executives to prioritize security
- Develops and promotes security awareness events that include employees and their families
- Frequently publishes relevant security event news and awareness updates